Defense
Future proofing defense

Why ?
Current defense systems face vulnerabilities from AI-driven attacks, IoT integration, and evolving cyber threats. secublox addresses these challenges with secure, tamper-resistant systems and transparent processes to ensure operational resilience, data integrity, and the safety of mission-critical assets.
01.
Identity and device management for
UAV Operations
02.
Access and mission management for multi-nation and multi domain command and control (C2) networks
01
Identity and device management for UAV Operations
Imagine a joint reconnaissance mission involving coalition drones patrolling a contested maritime region. When one drone detects an unauthorized submarine near strategic shipping lanes, it instantly shares tamper-proof data across a blockchain-enabled network. Allied assets—recon drones, naval vessels, and coastal centers—immediately receive verified threat information.
Smart contracts trigger coordinated responses, such as drones from Nations A and B forming a sensor perimeter and a submarine-hunting drone from Nation C deploying based on pre-approved engagement policies. Even amid communication disruptions, these assets autonomously collaborate under predefined rules, ensuring a unified, rapid, and effective defense that enhances situational awareness and leverages each asset’s strengths.
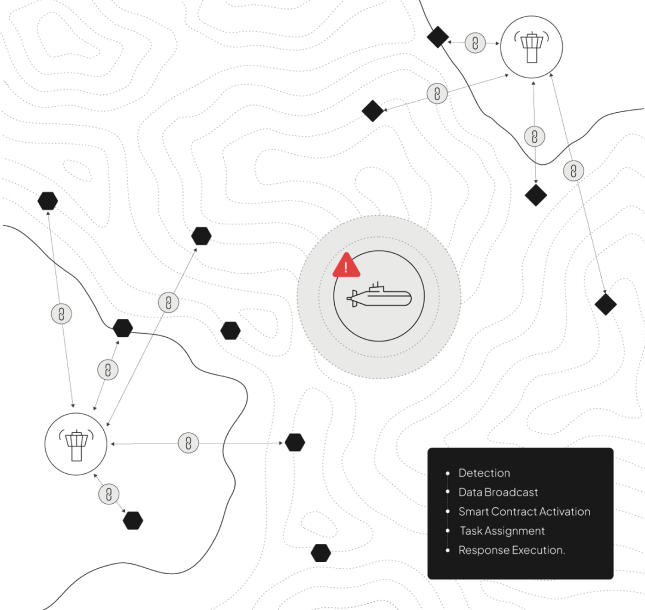
Key advancements driving Defense transformation
1 Federated Sovereignty
Decentralized governance with shared autonomy.
Enables partner nations to maintain control over their assets while participating in joint operations through secure digital platforms and blockchain-enabled networks.
2 Cross-Domain Data Fusion
Integrating data from multiple sources for unified insights
Integrates information across land, sea, air, and cyber domains for comprehensive situational awareness and coordinated response capabilities.
3 Autonomous Interoperability
Independent systems seamlessly working together.
Allows systems to communicate and coordinate automatically through smart contracts and blockchain, even during communication disruptions.
Secure, Real-Time Coordination Across Every Domain
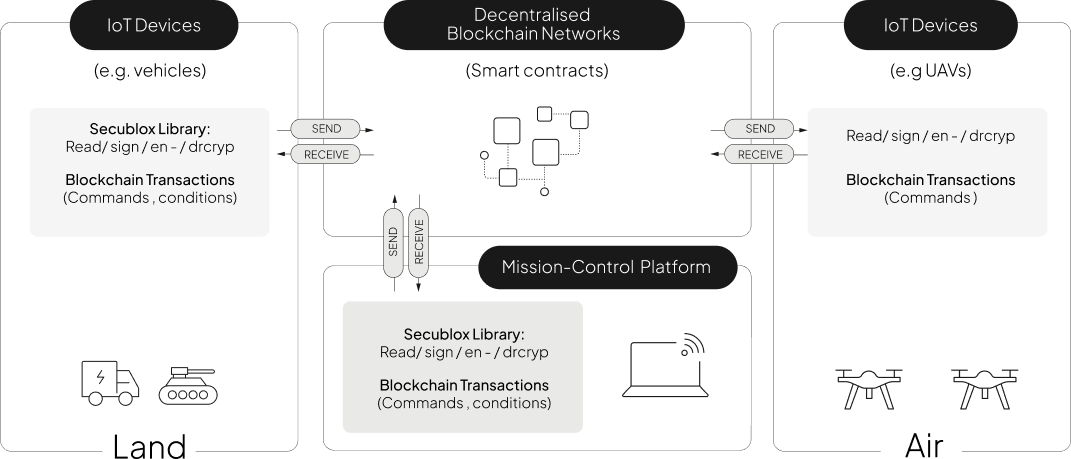
Modular system enhancing legacy architecture

Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat.
Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat nulla pariatur. Excepteur sint occaecat cupidatat non proident, sunt in culpa qui officia deserunt mollit anim id est laborum.
Strict Access Controls:
Distributed Resource Management:
A secure digital platform enabling partner nations and domains to jointly manage and allocate shared assets (e.g., aircraft, unmanned systems, advanced sensors, weaponry) with high levels of transparency and trust.
Complete Accountability
Dynamic Resource Allocation:
Automated, rules-based mechanisms to swiftly assign and reassign critical air systems and supporting technologies based on evolving operational needs, priorities, and mission profiles.
Seamless Integration with C2:
02
Access management for Multi-UAV command and control (C2) networks
- Multi-Domain Support: Air, land, sea, cyber, and space.
- Data Integrity: Immutable and tamper-proof.
- Encrypted P2P Communication: Advanced security for allied forces.

Imagine an FCAS mission where a sensor detects an enemy missile launch. In a blockchain-enabled network, that sensor could instantly share its data with every friendly asset in range – jets, ships, ground defenses, and command centers. Smart contracts built into the blockchain could automatically assign the best-placed units to respond, even if communications are jammed.
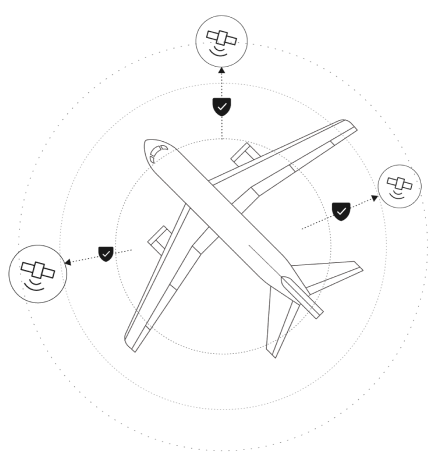

For Airbus secublox successfully developed a tech demonstrator within FCAS to jointly manage and allocate shared air assets (e.g., aircraft, unmanned systems, advanced sensors, weaponry) with strict access controls, ensuring transparency, trust, and dynamic resource allocation.
The solution provides complete accountability with detailed, unalterable records and seamlessly integrates with existing C2 systems for informed decision-making and enhanced mission effectiveness.
The future of defense lies in creating secure, interconnected ecosystems rather than merely adding new systems. Success depends on building trust networks that enable seamless information sharing while maintaining strict data privacy. Hello secublox.
